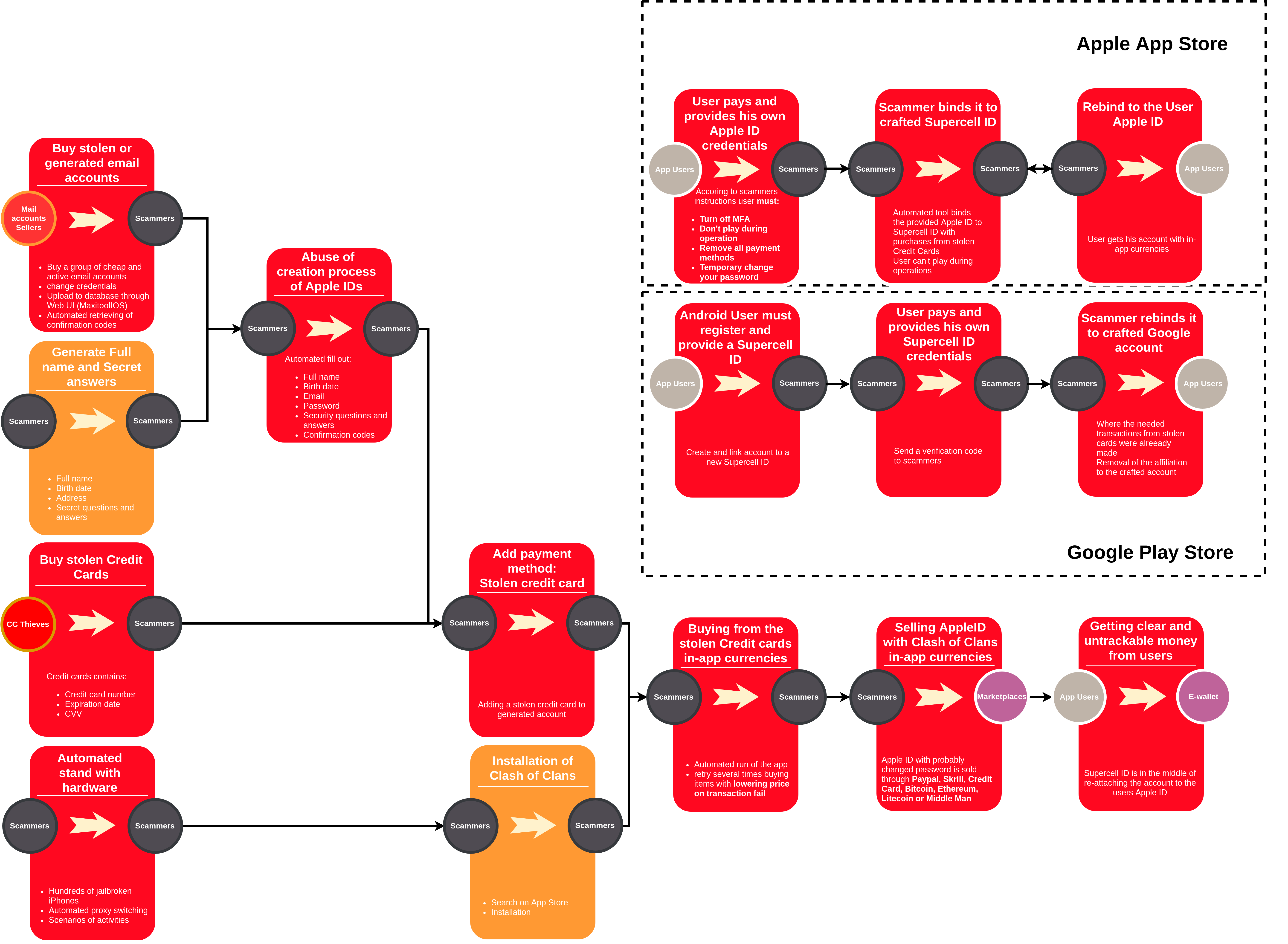
Clash of Clans, as well as Clash Royale and Marvel Contest of Champions are used in a major money laundering scam. Such a study was published by the German company Kromtech Security, specializing in cybersecurity.
How does the scheme work?
The scheme is based on the ability to sell accounts in free-play games to third parties.
With the help of an automated system, fraudsters easily register hundreds of fake accounts in games and connect stolen bank cards to them. The system buys in-game items in the game, after which it places an account for sale in a third-party store like g2g.com . The money for the sold accounts goes to the virtual wallets of scammers – thus the stolen card does not appear in the transaction.
In a simplified form, the fraudulent scheme looks like this (click to see the enlarged version):
And what are the volumes stolen?
As far as Kromtech Security knows, from the end of April to the middle of June, fraudsters laundered money from 20 thousand stolen bank cards through popular mobile frituplays. The credit cards belonged to 19 banks and were clearly bought on the black market in batches, because they were grouped into round amounts (such as 10k, 20k, 30k).
So far, fraudulent activity has been registered only in Clash of Clans (monthly revenue of $70 million), Clash Royale ($40 million) and Marvel Contest of Champions ($3 million). About 250 million users are registered in these games.
If a similar scheme is extended to other popular mobile games, the turnover of the black market accounts can reach billions of dollars, according to Kromtech Security.
Why is this so easy to pull off?
The loophole for scammers lies in insufficiently strict account verification systems in the App Store and Google Play. For example, Apple ID accounts created by the system were verified, despite errors in names and residential addresses.
Also, Apple apparently did not react to suspicious activity in any way – most of the accounts used by the scammers in Apple ID were verified within three April days.
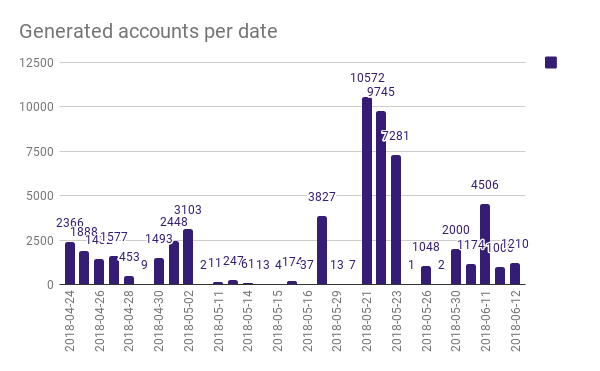
In addition, the verification system in mail domains turned out to be unsafe. So, in a short period of time, the system of scammers created 13 thousand mailboxes on Polish services without visible problems:
Finally, Kromtech Security believes that Supercell and Kabam, publishers of games through which money was laundered, do not sufficiently control user activity and do not ensure the safety of their players.
For example, experts found 176 pages on Google search, where players in Clash of Clans were tricked into offering free resources. Kromtech Security believes that Supercell itself can monitor such sites and seek their closure.
Experts also suggest banning accounts from which questionable purchases are made in the game, and tracking which card transactions were made from. Publishers can do this, but usually don’t.
Who is behind the scheme?
We are talking about one coordinated group of scammers. Their possible location has not yet been clarified, but Kromtech Security managed to track down a Facebook page in Vietnamese that could have been used by members of the group.
A certain tool was advertised on the page – apparently, the same automated system. Experts have determined that the system can be used in Saudi Arabia, India, Indonesia, Kuwait and Mauritania.
Is this the first time this has happened?
No. Money laundering through the AppStore and Google Play is not a new idea. In 2011, the top Danish App Store was unexpectedly flooded with suspicious premium apps. Each cost around $50-$100, most of them were from China.
The cost of the applications was completely unjustified – for example, the LettersTeach application for children to learn the English alphabet cost $78. Experts believed that these applications were part of some kind of money laundering scheme, and Apple removed them.
Also on the topic: